Resources for all, for a job that needs doing
From free software, to guides and recommendations, we can almost guarantee we've got something helpful here for you.
Did you know there are different kinds of hackers?
Well, they're all people at the end of the day, but there are different color "hats" depending on the hacker's talent and profession.
Learn what those colors are here.
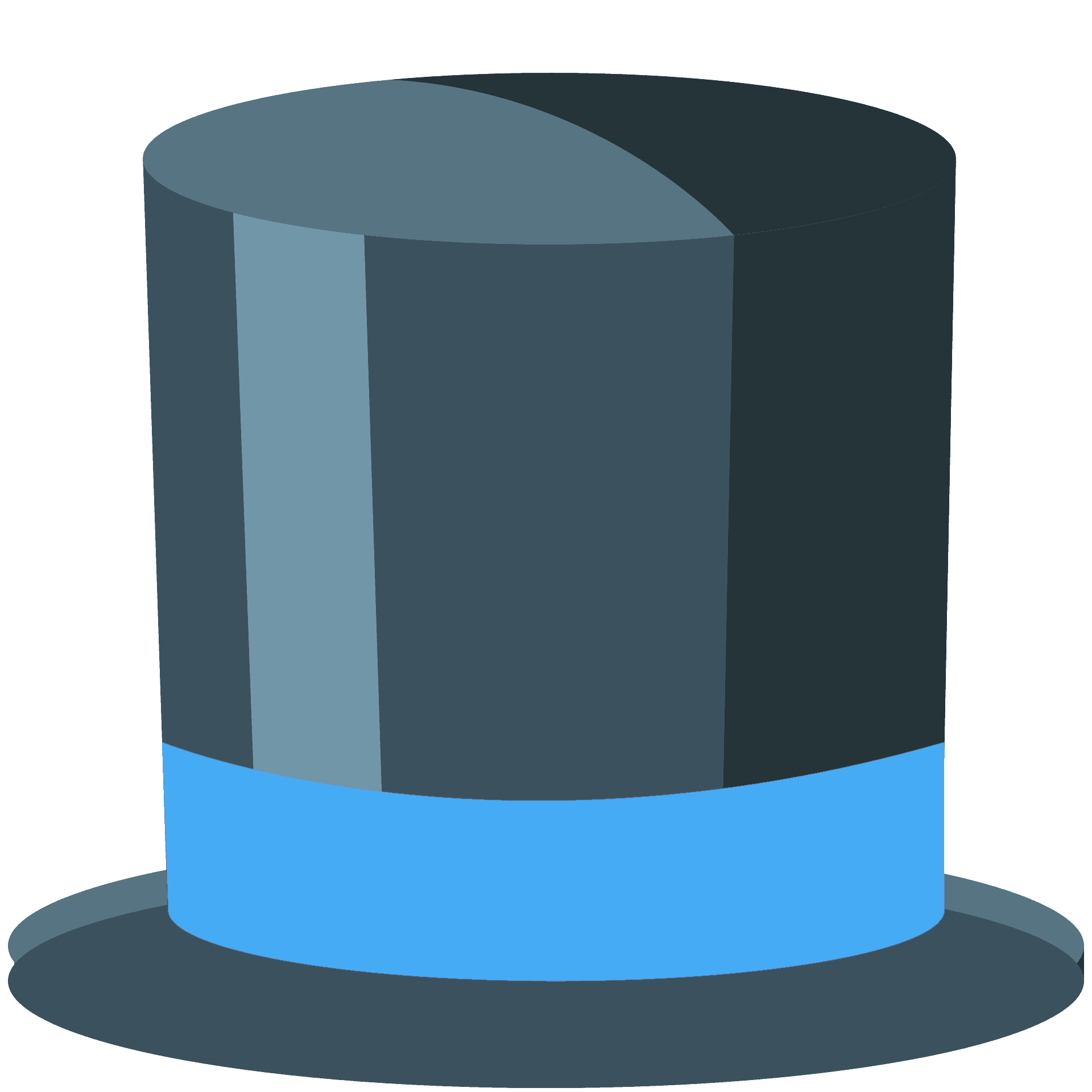
Good guys
Blue hats are defense-oriented ethical security researchers
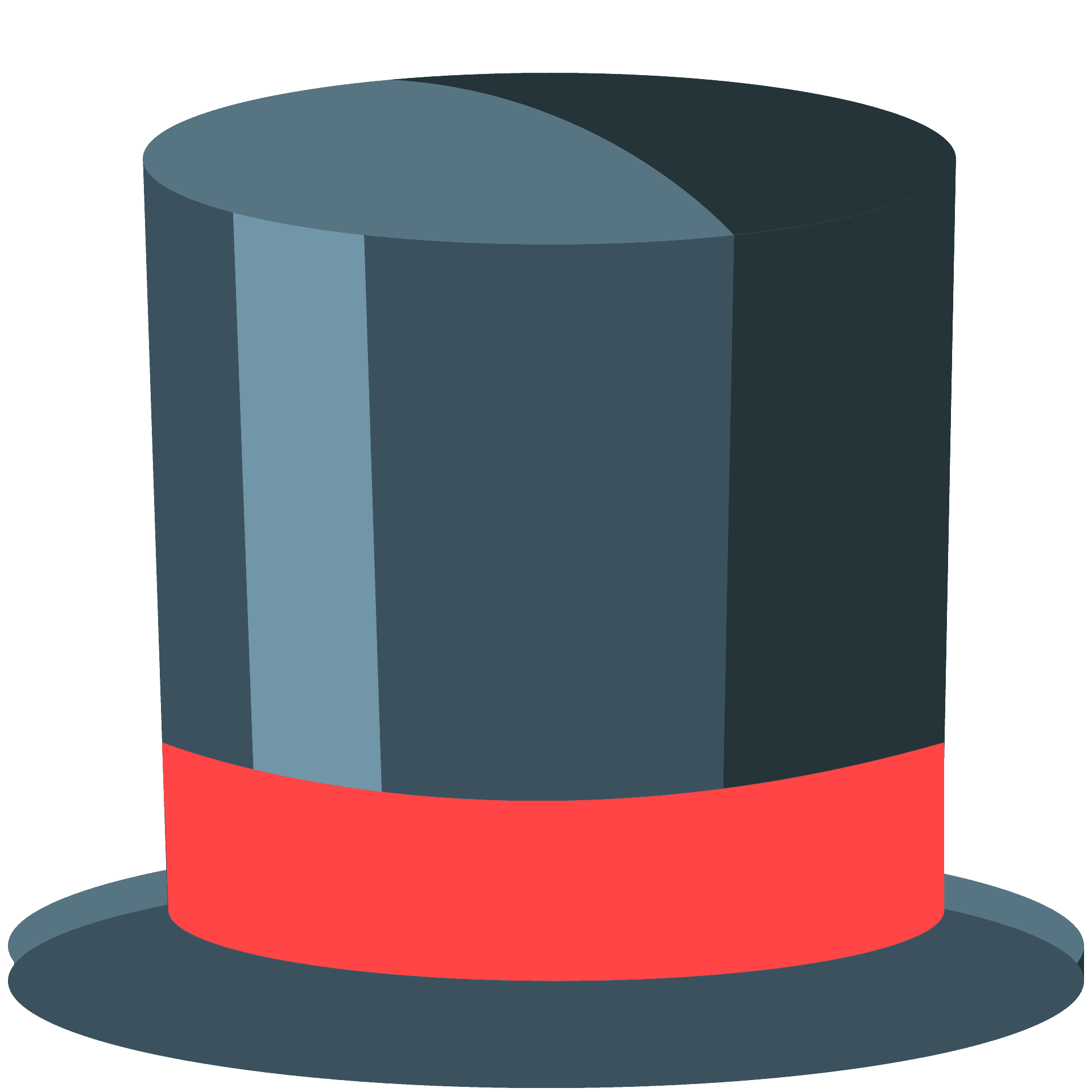
Good guys
Red hats are offense-oriented ethical security researchers
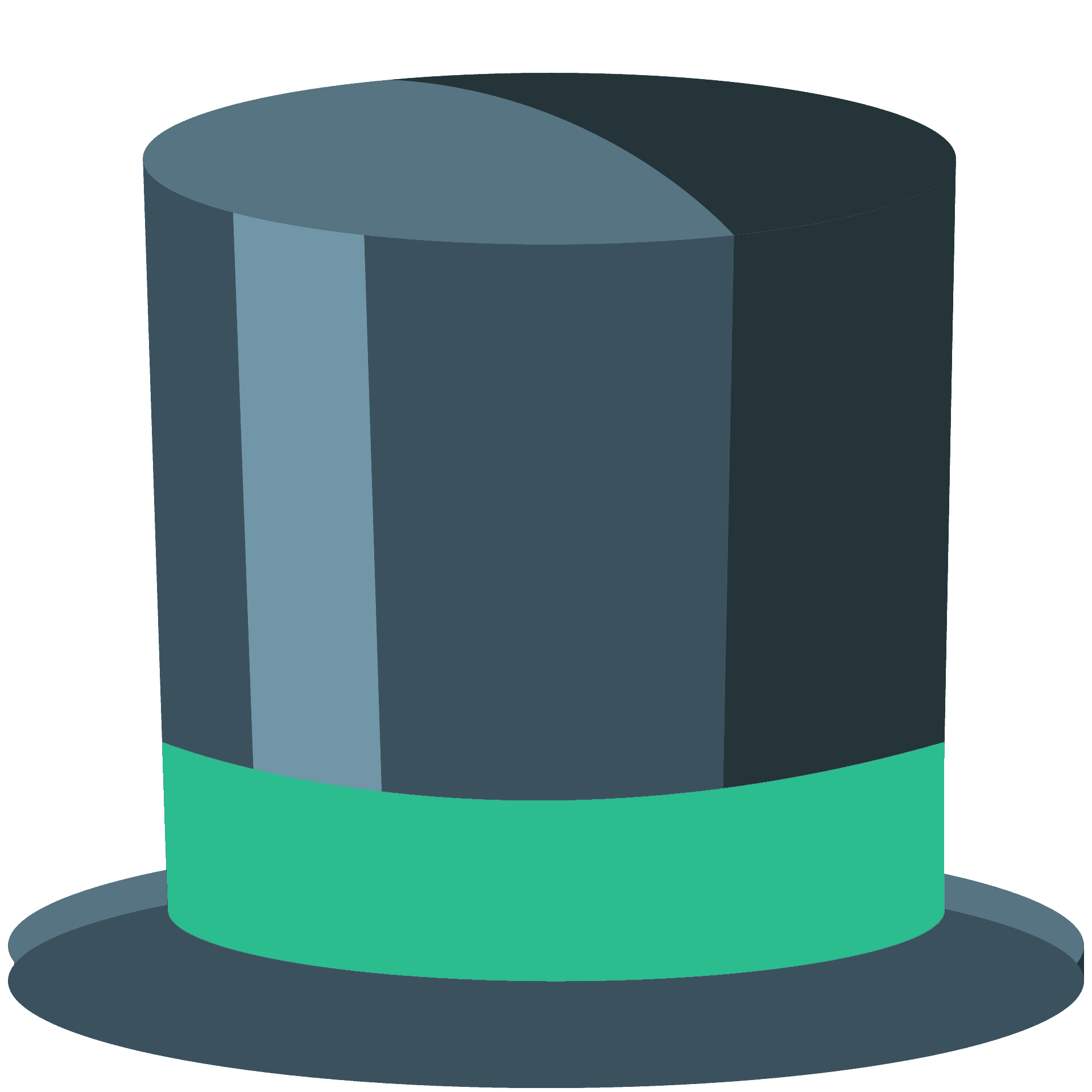
Good guys
Green hats are ethical security researchers who are still learning and maturing their tradecraft
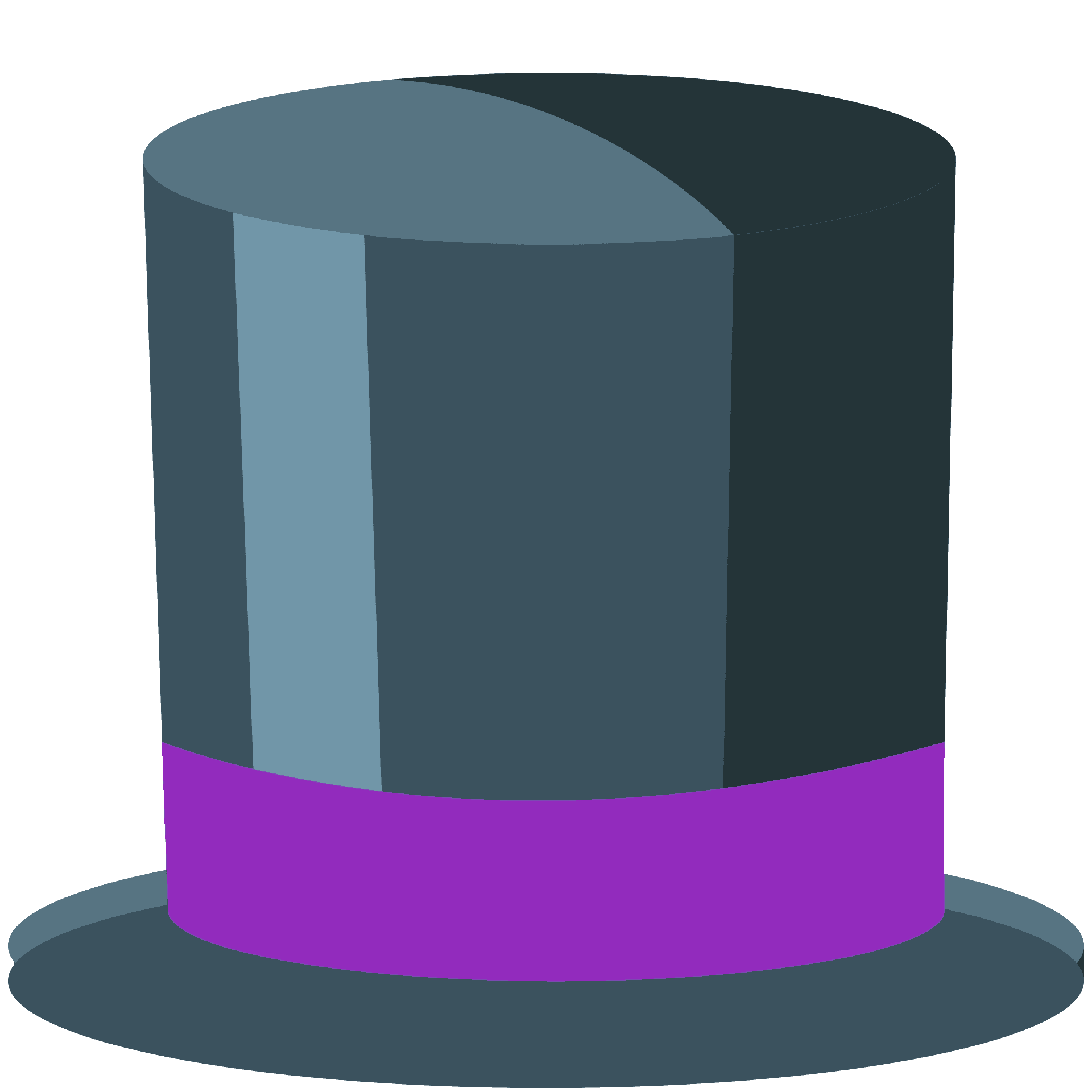
Good guys
Purple hats are ethical security researchers that practice both offensive and defensive security tradecrafts
Rarely a bad guy
White hats are "hackers" who place a high regard on laws, morals, and/or ethics during their operations. White hat hackers typically work with proactive respect to the law during their research efforts
Sometimes a bad guy
Grey hats are "hackers" who perform technically illicit actions during their operations to achieve success regardless of their means or motive, but infrequently target without cause. Think "Robin Hood Complex"
Always a bad guy
Black hats are "hackers" who intentfully seek to commit eCrime acts in part of, or as a whole of their operations. Ransomware actors are black hats, as an example
Blue hats
Red hats
Green hats
Purple hats
White hats
Grey hats
Black hats
Their tools?
Their knowledge?
Here, have it.
Our knowledgebase includes court case reviews and write-ups, documentation on a selection of offensive and defensive CyberTools, and much more!
Got something to add to it? Submit it in a Pull Request, and we'll accept it if it's high quality.
Looking for cloud hosting? virtual servers? object storage?
Unlock the full potential of your development projects with Linode's robust cloud hosting solutions. From deploying applications to managing databases and scaling infrastructure, Linode empowers developers with the flexibility and performance they need to bring their visions to life. With their intuitive control panel and comprehensive, class-leading API alongside developer-friendly documentation, managing your cloud infrastructure has never been easier. Whether you're building the next big app, running a high-traffic website, or experimenting with new technologies, Linode offers the reliability and scalability to support your endeavors.
Join the thousands of developers who have trusted Linode since 2003 for their hosting needs by using the link below to start with $100 free credit1 as a welcome bonus.
Analyzing files?
Use these tools and platforms for file analysis - they come highly recommended.
Tria.ge
A new malware sandbox, developed with scaling in mind from the start. Triage is Hatching’s new and revolutionary malware sandboxing solution. It leverages a unique architecture, developed with scaling in mind from the start. Triage can scale up to 500.000 analyses per day, an unprecedented number for a sandboxing service.